State-sponsored cyberattacks occur when the state directly employs cyber hackers through their militaries and government authorities, funding them indirectly. The state’s involvement and a twisted route to funding the attacks
Tag: data protection

Importance Of Email SecurityImportance Of Email Security
Ever since the move to remote and hybrid working models has been affected, communication among employees has become more exposed to risks and more essential to daily working life. An

The Repercussions of a Successful Phishing CyberattackThe Repercussions of a Successful Phishing Cyberattack
As seen in our previous Phishing blog, there are ways to spot Phishing emails. Disrupting business operations and orchestrating sophisticated data theft or money theft is the agenda for Cybercriminals.
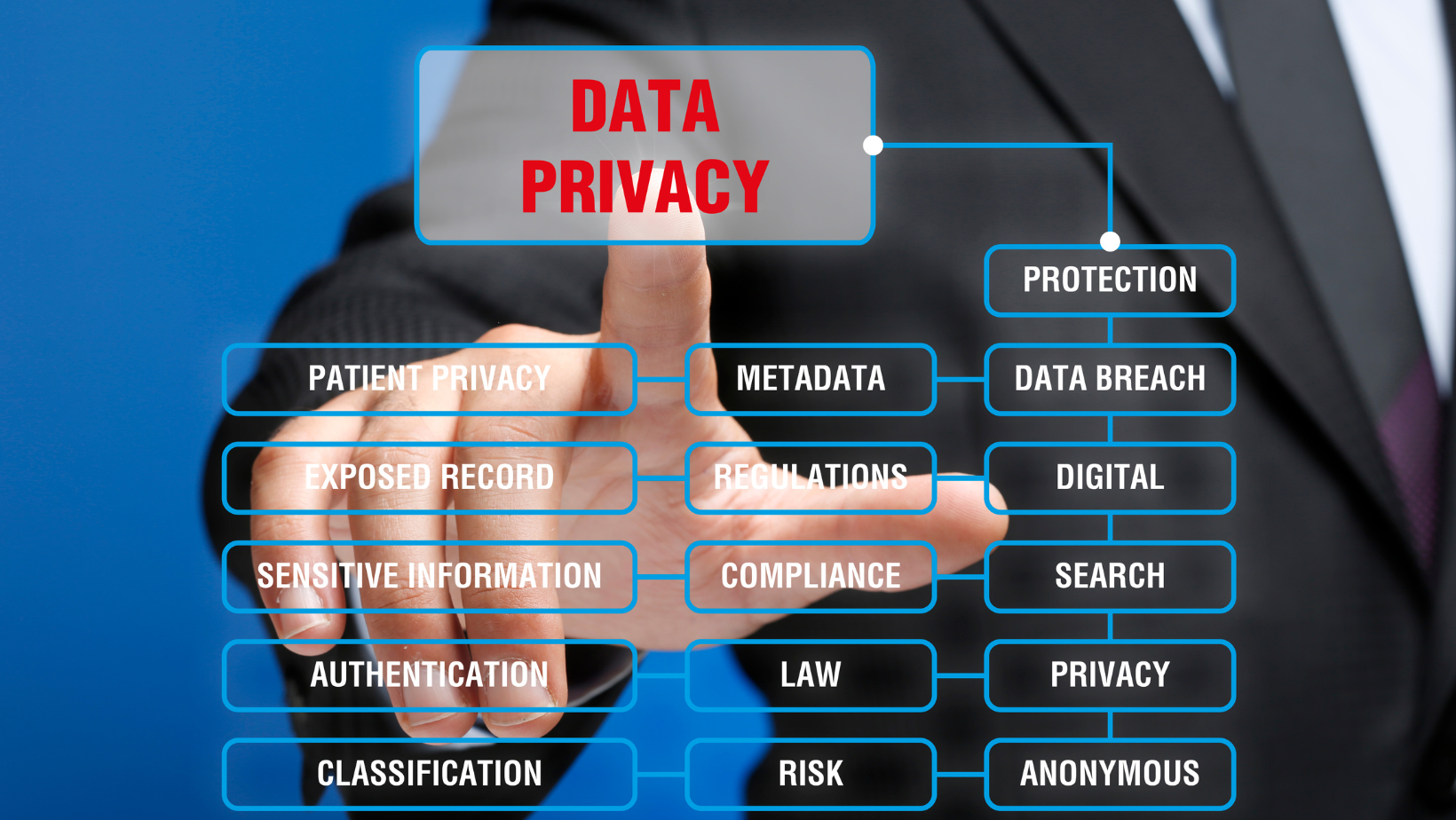
RECENT CERT-IN GUIDELINES AND DATA PRIVACY ISSUES IN INDIARECENT CERT-IN GUIDELINES AND DATA PRIVACY ISSUES IN INDIA
Virtual Private Server (VPS) providers, cloud service providers and VPN service providers. These guidelines have been issued under Section 70B of the Information Technology Act, 2000. However, the new guidelines

Safety Risks of Removable MediaSafety Risks of Removable Media
What Is Removable Media? Removable media can be understood as a portable storage medium that allows users to copy data from a laptop or system so that the data is

WHY SHOULD ONE AVOID USING FREE VPNWHY SHOULD ONE AVOID USING FREE VPN
Cybersecurity threats to businesses and individuals are increasing at a worrisome speed. It is a blessing, however, that consumers are also becoming somewhat more conscious of the amount of personal

SECURITY CONCERNS IN VIRTUAL REALITYSECURITY CONCERNS IN VIRTUAL REALITY
What is Virtual Reality?Virtual Reality is one of the latest trends in technology. It implies a computer-generated environment with scenes and objects that appear to be real, making the experience
FACEBOOK TO META- WHY THE NAME CHANGE?FACEBOOK TO META- WHY THE NAME CHANGE?
Since its inception, Facebook Inc has been one of the biggest trailblazers in the social media landscape. The concept of connecting with loved ones when it’s not practically possible to

NETWORK FIREWALL SECURITYNETWORK FIREWALL SECURITY
The network firewall is the first barrier for internet traffic that goes through a network. The firewall examines the web traffic to ensure it is secure as per the standards


