Deception technology empowers defenders by luring attackers to engage with fake assets, revealing their presence and tactics. In OT/IoT environments, deception plays a critical role for these 3 key reasons:
Category: blog

Avoiding the Clickbait Trap: How to Protect YourselfAvoiding the Clickbait Trap: How to Protect Yourself
Now more than ever, the world is a sea of information and all are fighting for our attention. Whether you are scrolling through your Facebook news feed, or browsing through

Protecting critical OT infrastructure with FortiNDRProtecting critical OT infrastructure with FortiNDR
Protecting your industrial mission-critical infrastructure is essential for maintaining safety and compliance. As per: Zscaler report 2024, Ransomware attacks in the Manufacturing sector increased 93.77% YoY. Palo Alto 2024 report

Defending Against Biometric AttacksDefending Against Biometric Attacks
As the use of new technology is embedded in our lives, it has never been more important to ensure our privacy and secure our data. Biometric technologies, such as fingerprint,

Secure the Serverless Frontier: Cloud Workload SecuritySecure the Serverless Frontier: Cloud Workload Security
As businesses change to use technology more, many are using serverless containers for their cloud. It empowers businesses to focus on innovation & development, instead of getting bogged down in

5 AI-Generated Scams in India: How to Stay Safe?5 AI-Generated Scams in India: How to Stay Safe?
Artificial intelligence (AI) is transforming many industries, including healthcare and finance. Like any technological advancement, AI also has new risks and vulnerabilities, especially in security. Another worrying development is the

What is Singularity MDRWhat is Singularity MDR
In today’s rapidly evolving threat landscape, staying secure demands both time & expertise. Singularity MDR is a new way to protect your endpoint devices. It gives you peace of mind

A Brief about Whale PhishingA Brief about Whale Phishing
A sophisticated and insidious cyber-attack gaining prominence is Whale Phishing. In contrast to typical phishing attacks, whale phishing or whaling targets important people like top management. In this blog, we
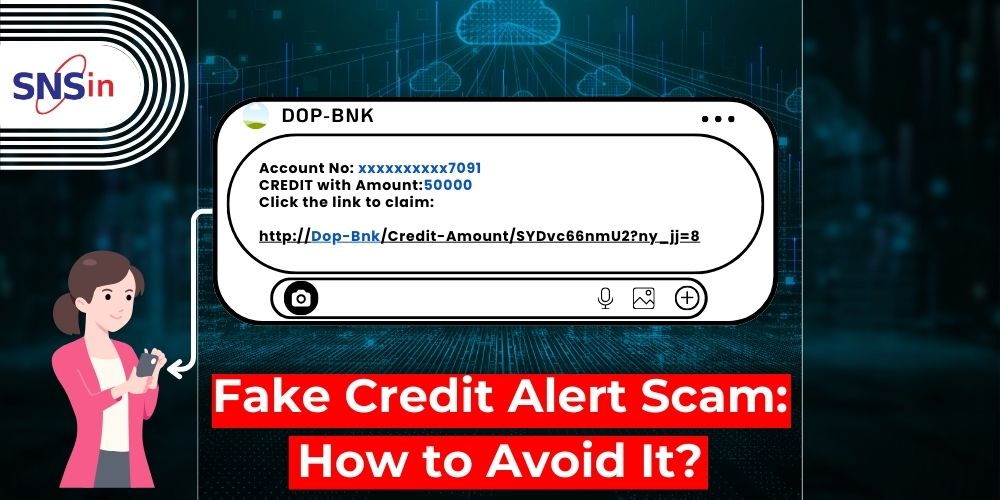
Fake Credit Alert Scam: How to Avoid It?Fake Credit Alert Scam: How to Avoid It?
Everything is going digital. It is common to find that financial transactions are quite easy and convenient. But this convenience has introduced a new level of threats and scams that
What is SentinelOne Singularity Endpoint?What is SentinelOne Singularity Endpoint?
Digital transformation is no longer a luxury but a necessity for businesses seeking to stay competitive. This brings a myriad of cybersecurity challenges, particularly endpoint security. As organizations expand their

